In today’s global marketplace, counterfeiting poses a significant threat to businesses, consumers, and economies worldwide. To combat this challenge, international standards like ISO 22383:2020 provide crucial guidelines for implementing effective authentication solutions. This blog explores the key authentication features outlined in ISO 22383:2020 and how Holostik’s comprehensive anti-counterfeiting portfolio addresses these standards.
What is ISO 22383:2020?
ISO 22383:2020 provides guidelines for performance criteria and evaluation methodologies for authentication solutions designed to establish material good authenticity and integrity throughout a product’s entire lifecycle. The standard focuses on authenticating:
-
- Material goods and their components
- Products covered by intellectual property rights
- Items covered by international, regional, or national regulations
- Products with counterfeiting-related implications
- Items with a distinctive identity requiring protection
Why ISO 22383:2020 Matters for Businesses?
This international standard helps organizations:
- Determine appropriate authentication elements needed to combat counterfeiting risks
- Establish criteria for selecting authentication elements after conducting a counterfeiting risk assessment
- Recognize that counterfeiting is a market reality acknowledged by governmental agencies
- Understand that overt, covert, and forensic features are industry standards
Identify reputable anti-counterfeiting solution providers (like Holostik) to address authentication challenges
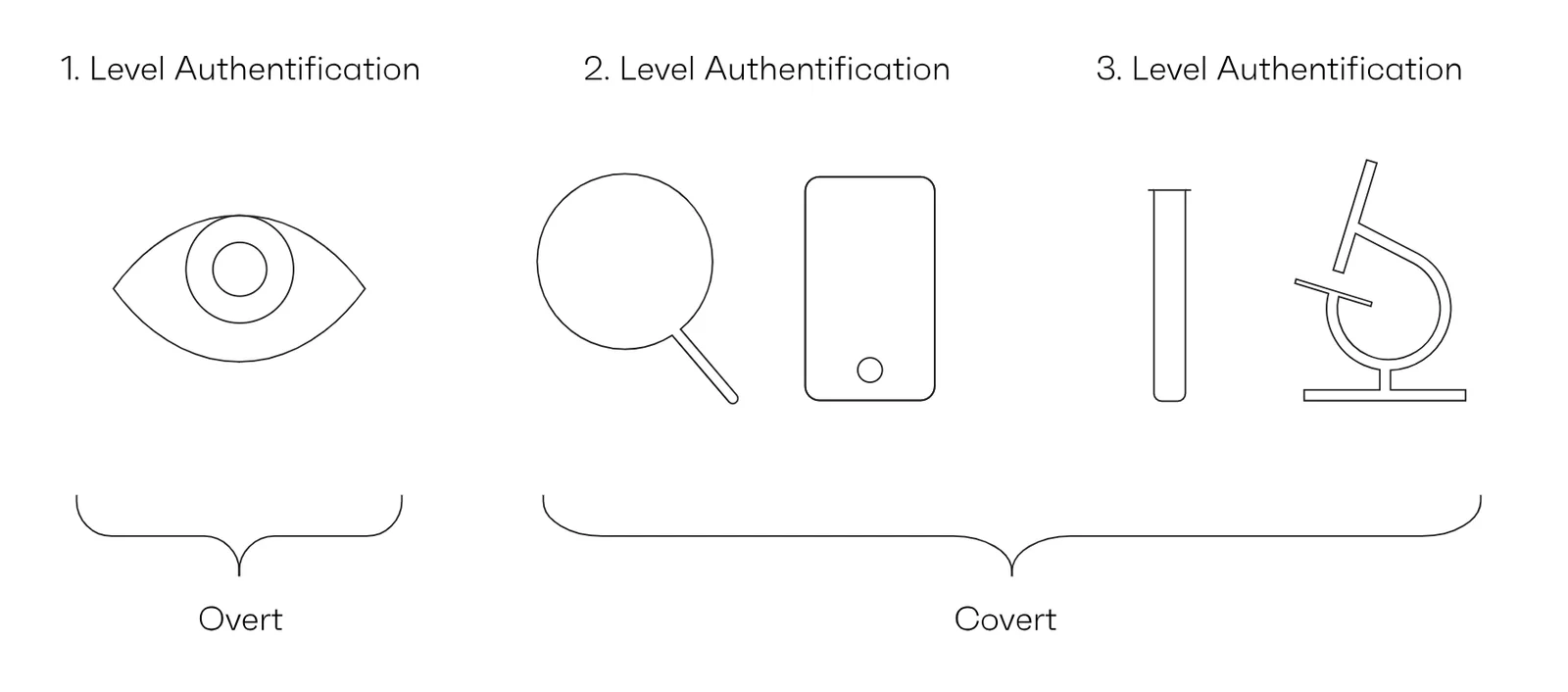
Breaking Down ISO 22383:2020: Authentication Features
ISO 22383:2020 categorizes authentication solutions based on:
- The human senses involved
- Required authentication tools
- The intended audience (general or restricted)
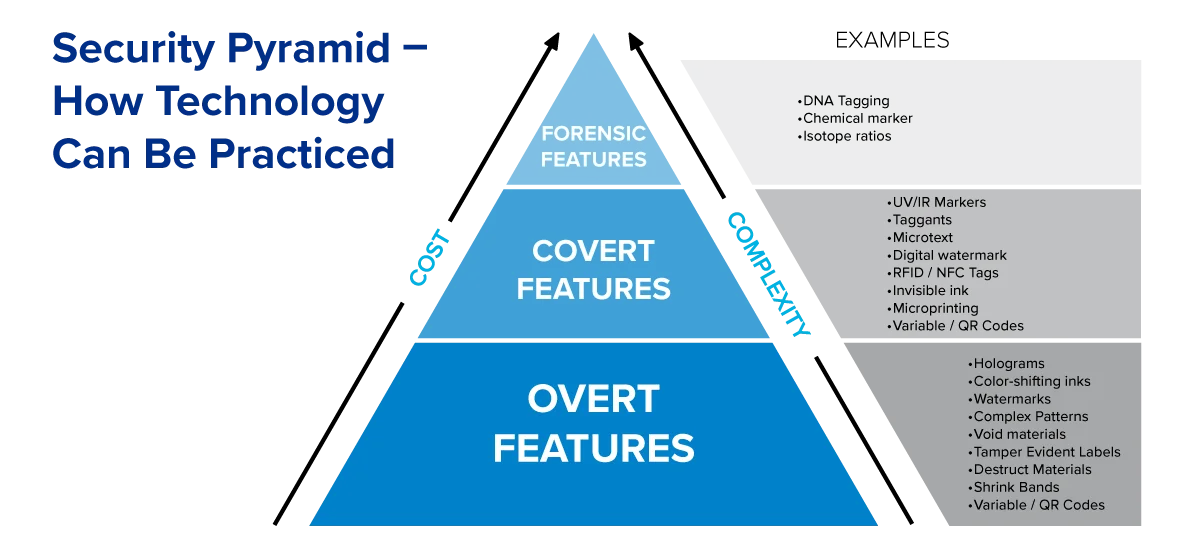
The standard emphasizes three primary types of authentication features:
| Feature Type | Human Sense | Authentication Tool | Intended Audience |
| Overt | Visible to human senses | None or simple tools | General & Restricted |
| Covert | Not immediately detectable | Required specialized tools | Restricted |
| Forensic | Laboratory detection only | Advanced analytical equipment | Highly Restricted |
Let’s explore each feature type in detail:
Overt Authentication Features
What are Overt Authentication Features?
Overt features are immediately apparent to human senses, primarily sight and touch. They provide first-line defense against counterfeiting by enabling quick visual verification without specialized equipment.
Why are Overt Features Important?
Overt authentication elements are crucial where immediate visual checks are the only verification possible. They empower:
- Consumers to verify product authenticity at point of purchase
- Store clerks to quickly identify potential counterfeits
- Supply chain personnel to perform rapid authenticity checks
Holostik’s Overt Authentication Solutions
Holostik offers an extensive range of overt authentication features in their security products:
| Overt Feature | Description |
| 2D/3D Depth Effects | Visual depth perception creating dimensional appearance |
| Dynamic Effects | Motion and animation visible when tilting |
| Kinetic Effects | Movement illusions with angle changes |
| Channel Effects | Color-shifting elements with up to 4 channels |
| Lens Effects | Magnification and optical distortion |
| Pearl Effects | Iridescent, color-shifting appearance |
| Guilloche Patterns | Complex, precise geometric patterns |
| Emboss Effects | Tactile raised elements |
These features are incorporated across Holostik’s product lineup including Security Holograms (OVDs), Hot Stamping Foils, Revenue Stamps, and Holographic Packaging.
Covert Authentication Features
What are Covert Authentication Features?
Covert features are not immediately recognizable or interpretable by human senses alone. They require specialized authentication tools and/or knowledge to verify their presence and validity.
Why are Covert Features Important?
Covert technologies exploit physical, chemical, or biological effects that are difficult for counterfeiters to replicate. These features provide:
- A second layer of authentication for authorized personnel
- Higher security for high-value products
- Technical barriers against sophisticated counterfeiters
Holostik’s Covert Authentication Solutions
Holostik incorporates sophisticated covert features across their security product range:
| Covert Feature | Description |
| Raster Text/Images | Hidden images visible with specific viewers |
| CLR Text/Images | Concealed elements revealed with laser readers |
| Microtext | Tiny text requiring magnification |
| Micro Photo/Images | Microscopic images requiring magnification |
| Micro Structures | Precise microscopic patterns |
These covert elements are strategically integrated into Holostik’s Security Labels & Smart Labels, Security Pouches, and Induction-Sealing Wads.
Forensic Authentication Features
What are Forensic Authentication Features?
Forensic authentication elements require dedicated methods, tools, and laboratory analysis to verify authenticity. They represent the highest level of security.
Why are Forensic Features Important?
Forensic authentication provides:
- Court-admissible evidence of counterfeiting
- Ultimate verification for high-risk products
- Definitive authentication for disputed cases
Holostik’s Forensic Authentication Solutions
Holostik’s advanced forensic features include:
| Forensic Feature | Description |
| Nano Text | Submicroscopic text requiring laboratory equipment |
| Forensic Markers | Chemical or molecular taggants |
| Spectral Signatures | Unique spectroscopic responses |
Holostik’s Integrated Authentication Approach
Holostik’s comprehensive anti-counterfeiting portfolio combines these authentication features into a multi-layered security approach:
Digital Authentication Extensions
Beyond physical security features, Holostik offers digital authentication solutions that complement ISO 22383:2020 guidelines:
- Track & Trace systems for supply chain visibility
- Mobile authentication applications like SureAssure for consumer verification
- Customized authentication solutions for specific industry needs
How Customers Can Benefit from ISO 22383:2020 and Holostik Solutions?
Organizations implementing authentication solutions aligned with ISO 22383:2020 can:
- Protect Brand Reputation – Prevent counterfeit products from damaging brand perception
- Ensure Consumer Safety – Verify product authenticity to protect consumers from potentially harmful counterfeits
- Safeguard Revenue – Reduce sales losses to counterfeit products
- Enhance Supply Chain Security – Monitor product movement and detect potential security breaches
- Demonstrate Compliance – Meet regulatory requirements for product authentication
- Build Consumer Trust – Provide visible security features that reassure consumers of authenticity
ISO 22383:2020 provides a robust framework for implementing effective authentication solutions. By understanding the distinct roles of overt, covert, and forensic features, organizations can develop comprehensive anti-counterfeiting strategies tailored to their specific needs.
Holostik’s diverse portfolio of security solutions – from Security Holograms and Hot Stamping Foils to Smart Labels and Security Packaging – aligns perfectly with ISO 22383:2020 guidelines. By implementing these multi-layered authentication solutions, businesses can protect their products, brands, and customers from the growing threat of counterfeiting.
Contact Holostik today to develop a customized authentication strategy that meets ISO standards and provides the protection your products deserve.

